A series of recent events prompted us to analyze cybersecurity and the risks associated with outsourcing it.
First, on July 19th, a CrowdStrike update caused a major outage, affecting 8.5 million devices. As a result, CrowdStrike’s stock has already plummeted by around 15%, or roughly $300 million, due to the incident. Theories about what happened range from a simple mistake to something more sinister, but the details remain unclear. Several theories have emerged:
- Coding mistake. Security researcher Zack Vorhies (@perpetualmaniac) suggests a simple coding error could be to blame.
- Quality control failure. The update might have bypassed safeguards meant to catch such errors.
- Organizational issues. Some speculate that CrowdStrike may prioritize sales over rigorous software quality control.
This isn’t the first time an antivirus update has caused widespread issues. In 2010, McAfee accidentally removed a crucial Windows file, incapacitating millions of Windows XP machines. Interestingly, George Kurtz, now CEO of CrowdStrike, worked for McAfee in 2010 during their own antivirus mishap. What a coincidence!
But that’s not all… On September 1st, Politico reported a major breach in New Hampshire. The state entrusted a newly formed IT company, WSD Digital, to update its 2024 U.S. presidential election voter registration database. However, it was discovered that the company had outsourced part of the work offshore, using a free software library created by Russian developer Denis Pushkarev, who has a criminal past (he had bitten a woman to death, was sentenced for years but got out of the jail in 10 months). This raised concerns about the potential involvement of Russian special services, especially since the software allowed connections to servers in other countries, including Russia.
These incidents raise a crucial question: Is outsourcing cybersecurity truly safe and better than managing it in-house, given that both approaches can lead to significant breaches? Or is there a third option?
Content:
- Cybersecurity statistics 2024-2025
- Staff augmentation – a perfect solution for delegating cybersecurity
- How do you keep your data safe when working with third-party vendors?
- Your fears are irrational – here’s why
- MWDN – your reliable cybersecurity partner
Cybersecurity statistics 2024-2025
The cybersecurity industry has grown rapidly due to the increasing amount of sensitive information stored online. Companies need stronger protection for trade secrets, confidential data, and personal information. As internet use rises globally, once seen as just an IT task, cybersecurity is now a key part of top-level strategic planning, especially with the expectation of 20 billion IoT devices by 2028.
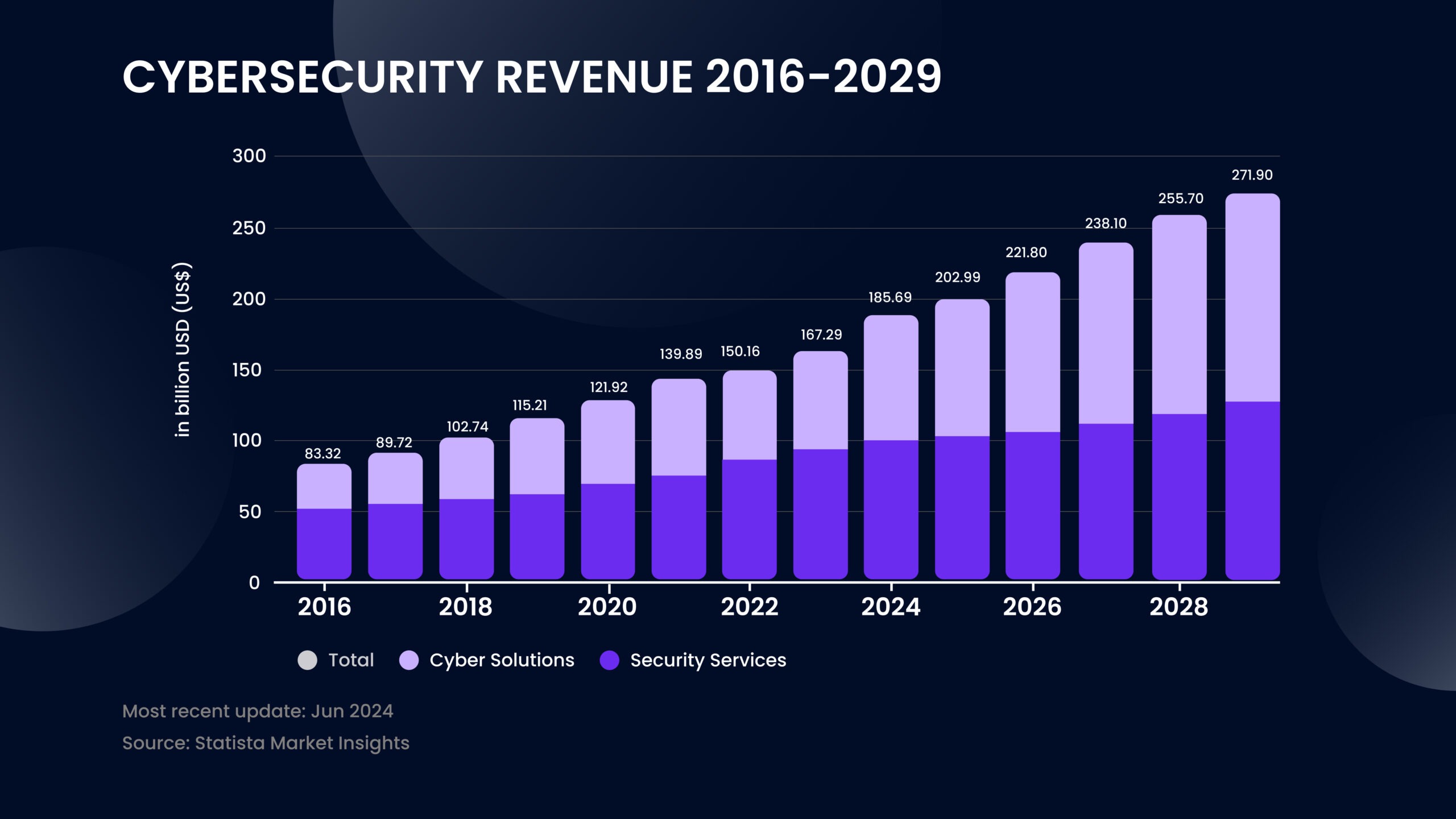
Cybersecurity revenue 2016-2029
The COVID-19 pandemic and events like the Russia-Ukraine war have increased cyber threats, pushing businesses to invest more in security. In 2023, global cybersecurity revenue reached $167.3 billion and is expected to rise to $271.9 billion by 2029, covering both security services and cyber solutions.
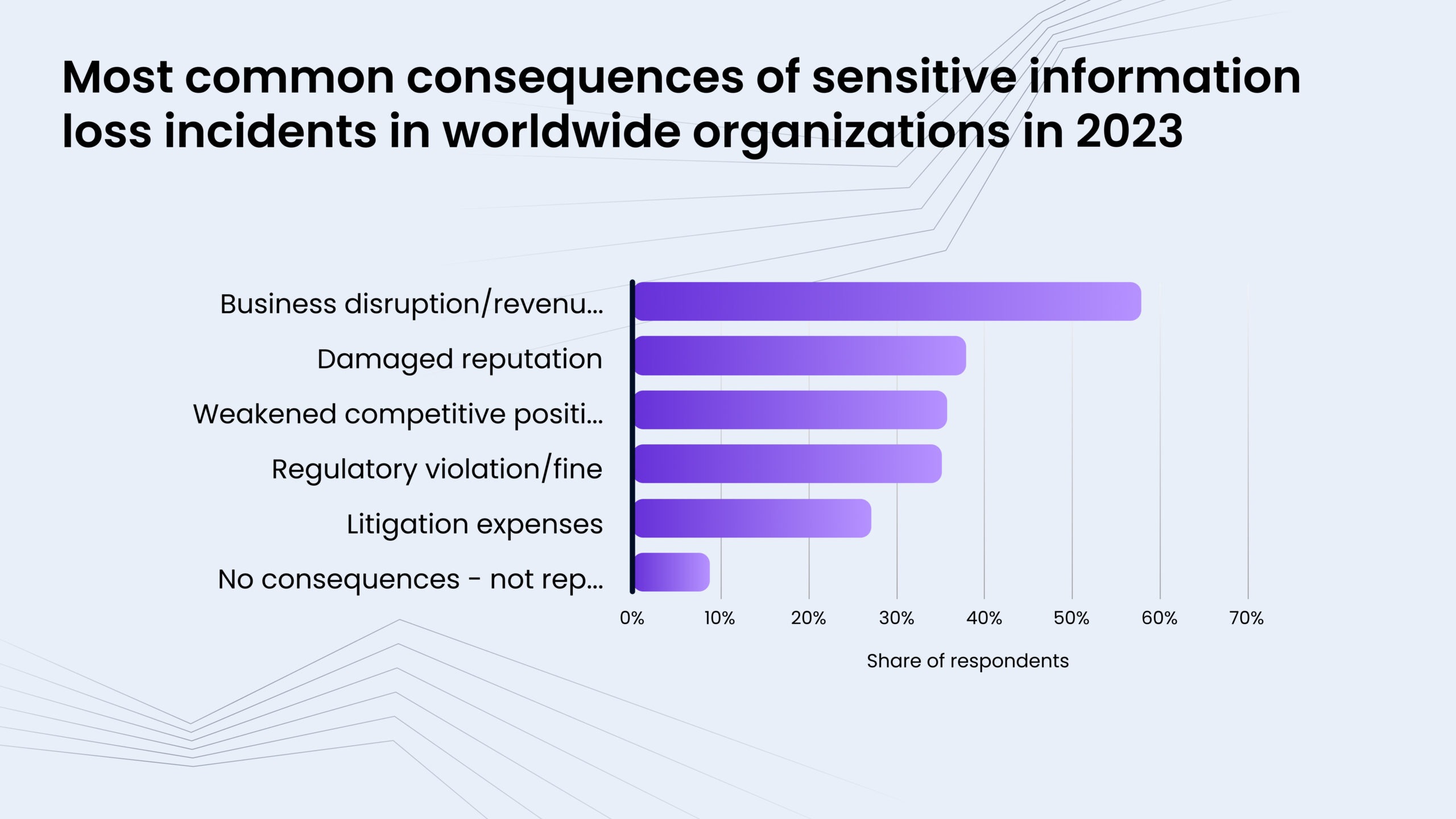
Consequences of cybersecurity incidents for business
Cybercrime comes in many forms, including identity theft, data breaches, ransomware, copyright violations, and phishing. One of the biggest concerns for companies is losing personal data of customers or employees, as it can lead to serious consequences like reputational damage and revenue loss. A 2023 survey found that 56.6% of companies worldwide faced business disruptions and lost revenue due to sensitive data breaches. Nearly 40% also suffered damage to their reputation. Other consequences included losing their competitive edge, breaking regulations, and facing fines.
Source: Statista
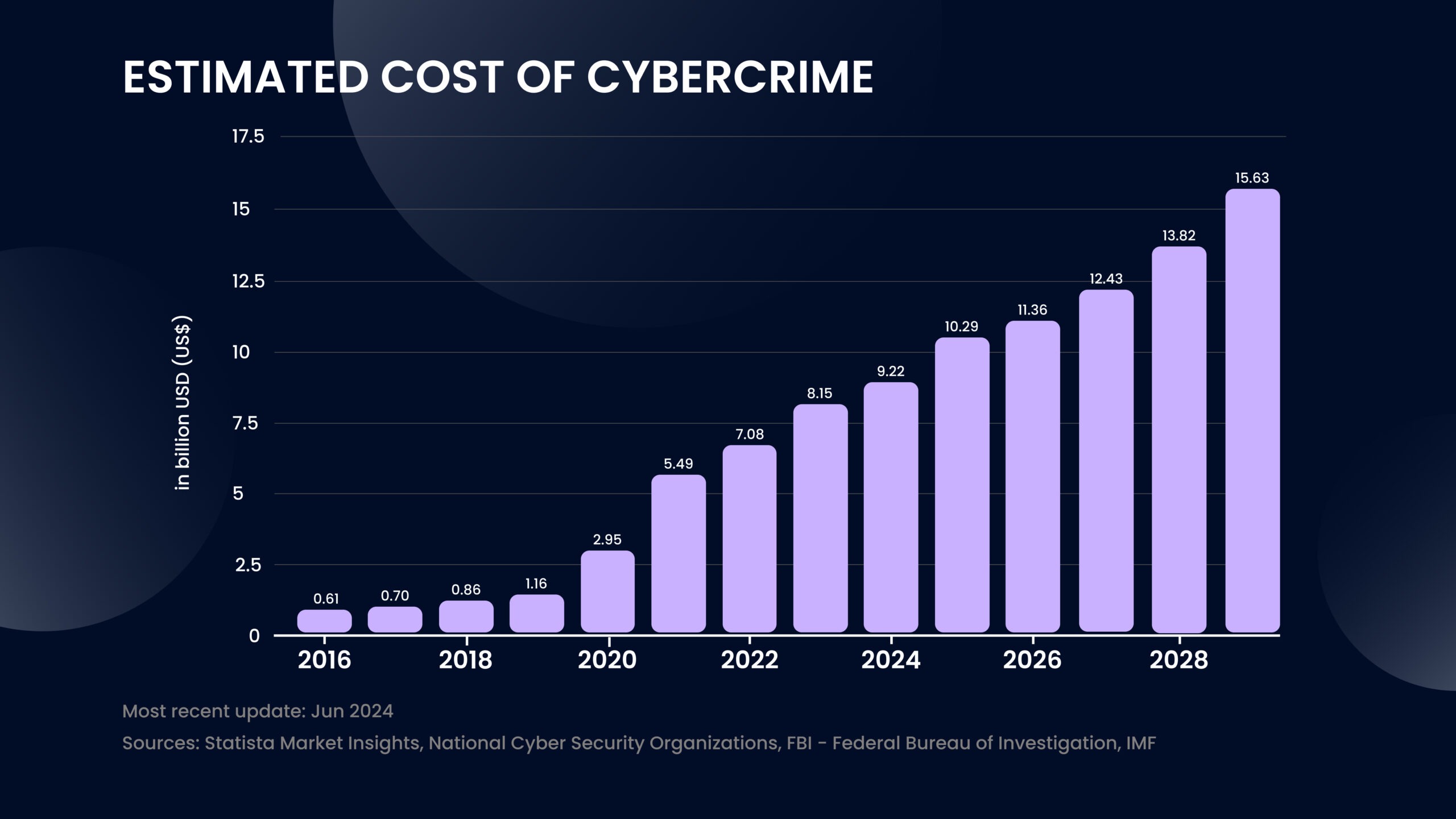
The cost of cybercrime
Companies worldwide not only pay to recover lost data from cyberattacks but also face downtime and operational disruptions. The average global cost of a data breach is about $4.35 million, though this can vary by region, company size, and industry. In healthcare, the average cost is even higher, at $10.1 million per breach.
In 2025, the estimated cost of cybercrime is expected to be 10.29 million US dollars per cybercrime.
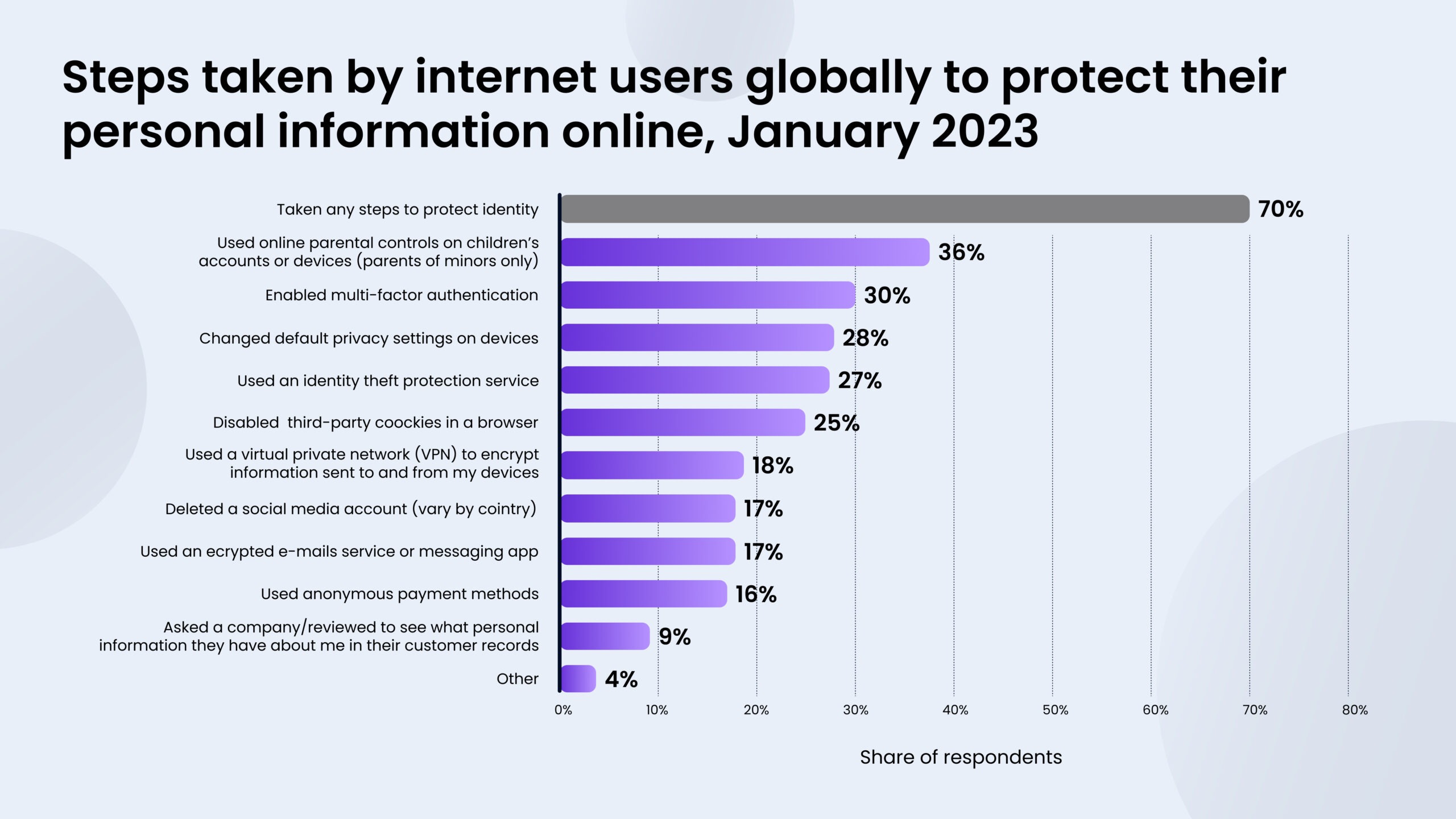
Actions to safeguard personal information
As governments work to improve personal data protection, more people become aware of online risks and take steps to protect their identity. In 2023, 70% of internet users reported taking action to safeguard their personal information. However, some are still willing to accept risks for easier internet use. Nearly 70% of people worldwide also said they feel more vulnerable to identity theft now than they did in the past.
The key statistics for business owners
However, the most interesting piece of statistics for companies and business owners is the average spend per employee on cyber solutions and security services.
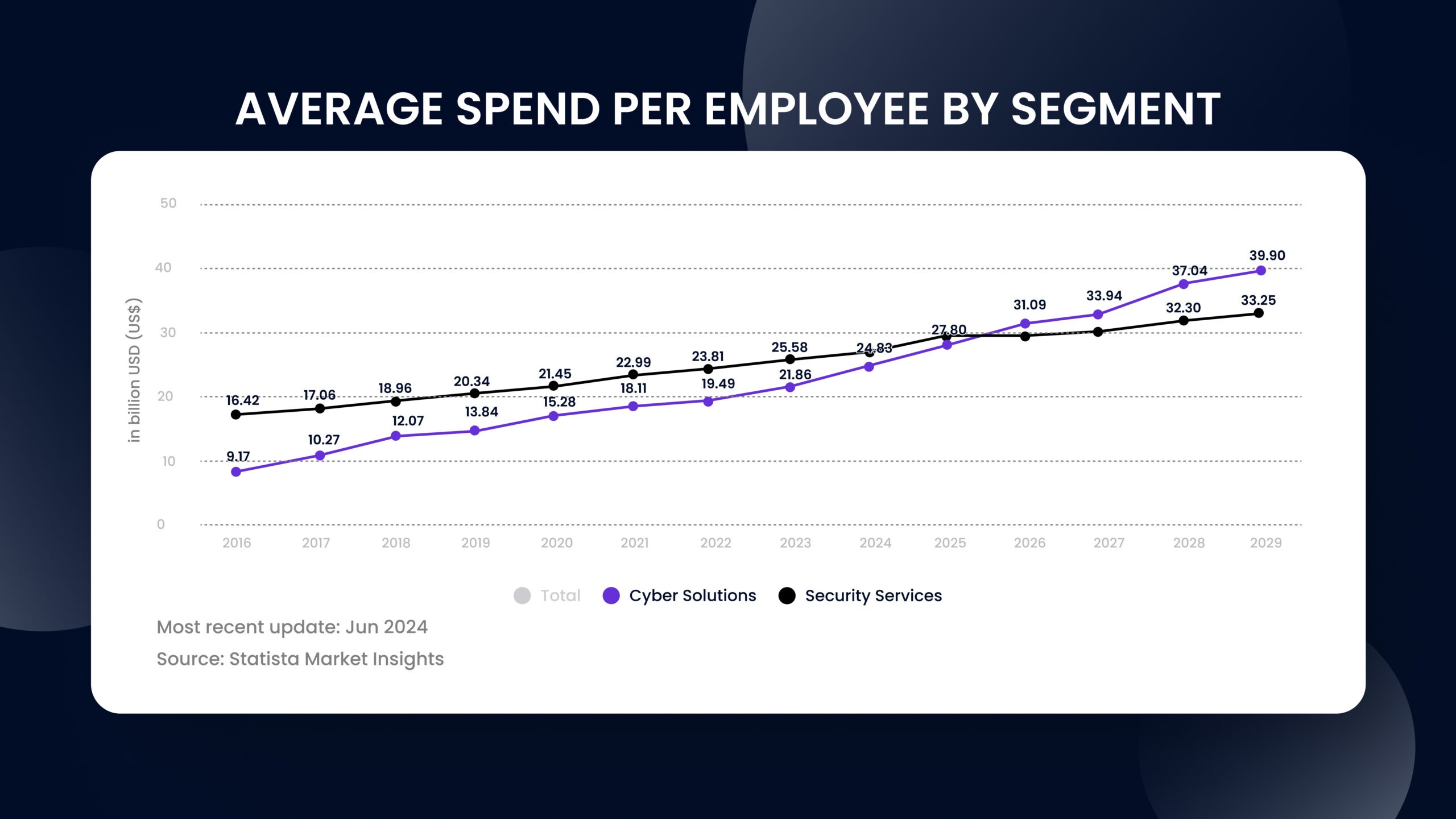
In this context, spend per employee is the amount of money a company invests on cybersecurity per employee in areas like cyber solutions and security services. This figure represents the company’s costs for providing cybersecurity protection per employee, such as:
- Purchasing and maintaining cybersecurity software and tools (like firewalls or encryption systems).
- Contracting security services (like monitoring, threat detection, or incident response).
- Ensuring compliance with cybersecurity regulations and securing systems against cyberattacks.
It’s a measure of how much a company invests in securing its employees’ access to digital resources and protecting the overall infrastructure against cyber threats.
Seeing that this number continues to grow, you might wonder: What can you do to cut these costs without compromising security? One option is staff augmentation.
Staff augmentation – a perfect solution for delegating cybersecurity
Outstaffed teams offer several advantages over in-house teams and traditional outsourcing, particularly regarding flexibility, cost, and access to specialized skills. Below are some of the staff augmentation benefits for your business.
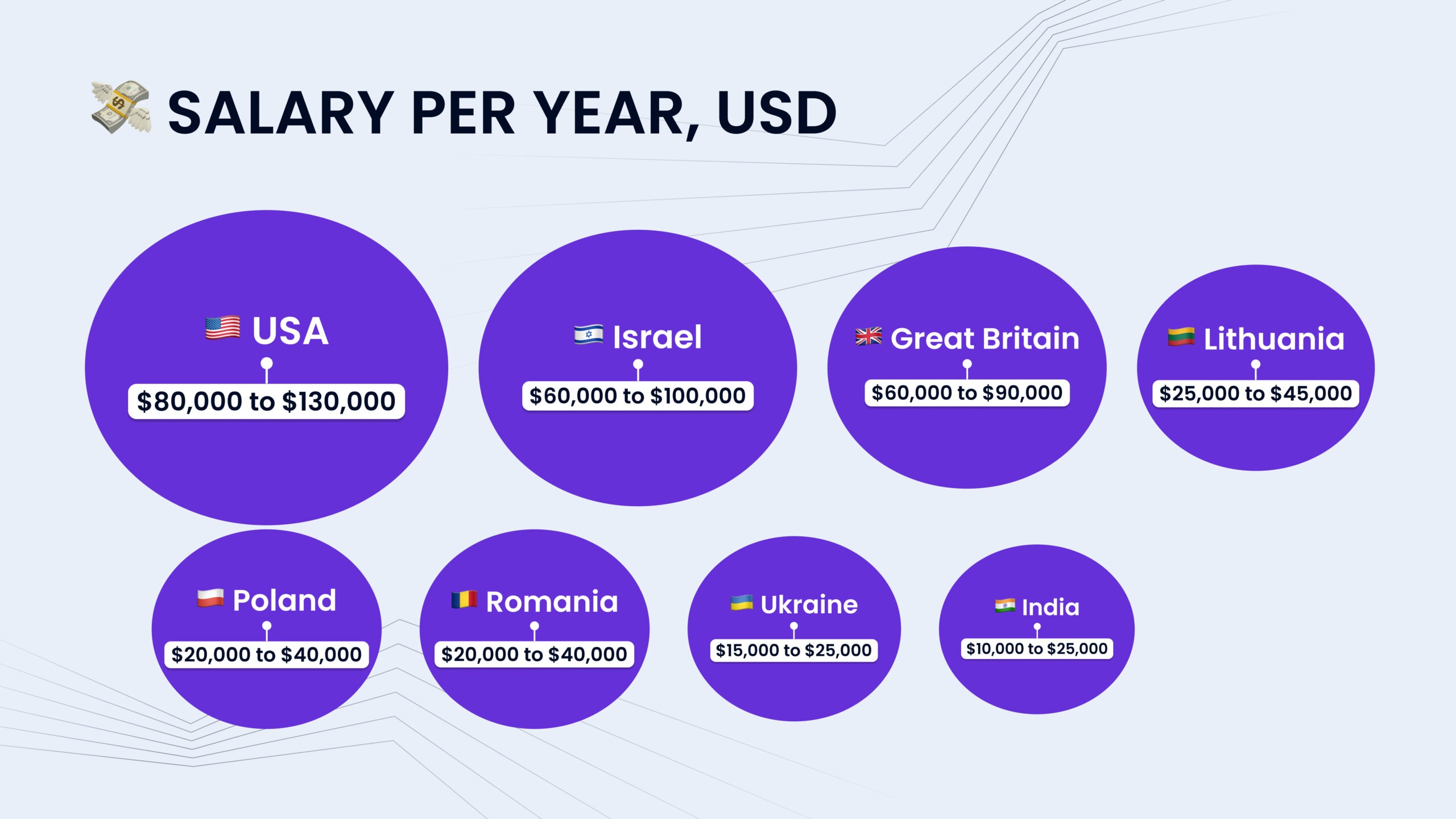
1. Lower direct labor costs
With outstaffing, you can hire tech talent in regions with lower labor costs. For example, hiring cybersecurity specialists in Eastern Europe or Asia can be significantly less expensive than hiring locally in high-cost regions like North America or Western Europe. Here’s a quick example of how much a cybersecurity specialist makes depending on their residence:
2. Reduced overhead
Outstaffing eliminates the need for office space, utilities, equipment, and other overhead costs typically associated with maintaining an in-house team. Here’s a quick breakdown of how staff augmentation can save you a fortune!
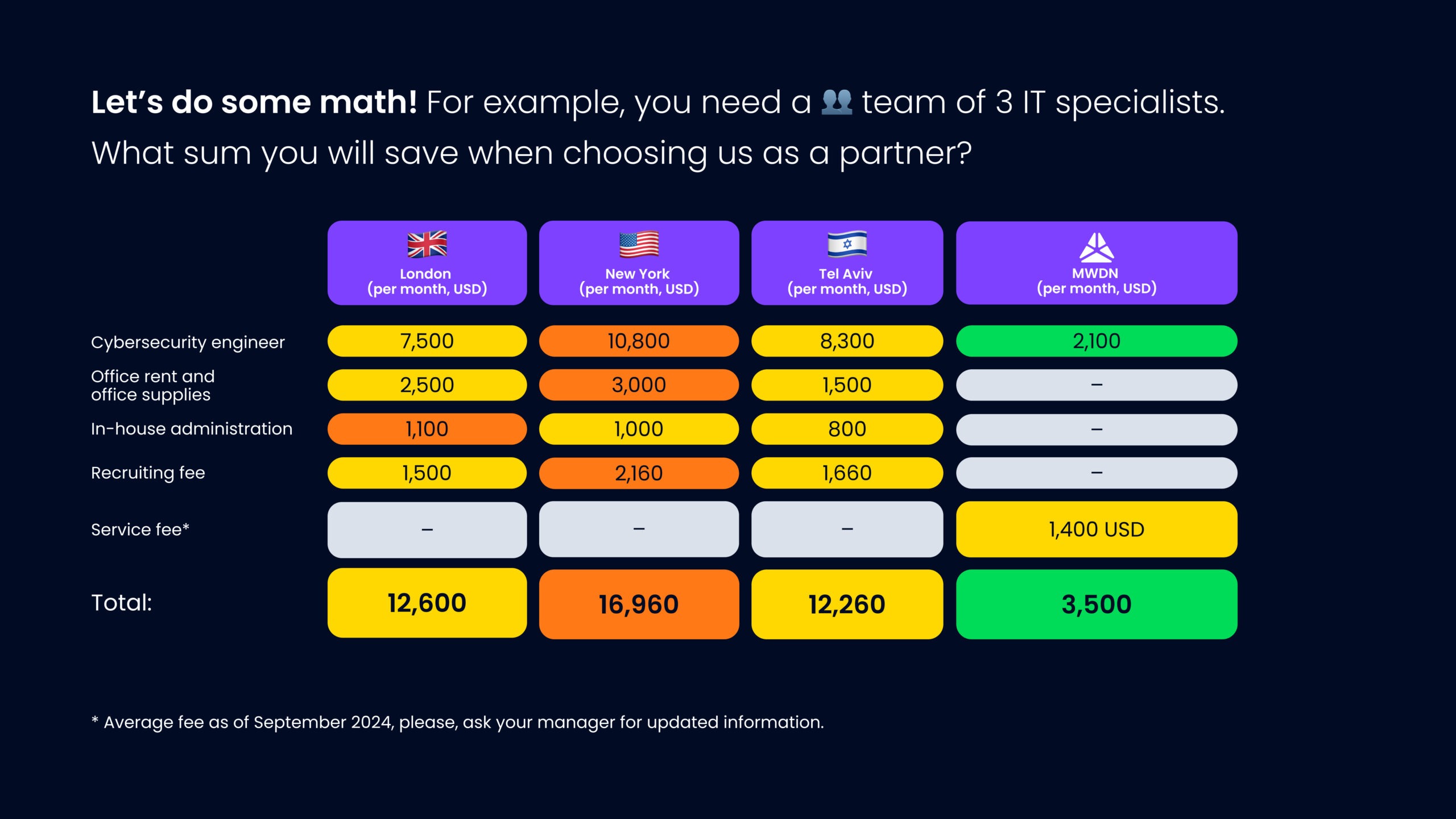
* Average fee as of September 2024, please, ask your manager for updated information.
3. Specialized expertise
Outstaffing provides access to a global talent pool, making it easier to find professionals with niche skills or specific industry expertise. This is particularly valuable for projects requiring specialized knowledge that might be scarce locally.
Working with a globally distributed team also brings diverse perspectives and innovative ideas, enhancing creativity and problem-solving.
4. Fast scaling
Outstaffing helps you scale your teams based on your project needs. This flexibility is crucial for businesses that experience fluctuating workloads or seasonal demands.
Apart from that, you can easily adapt to changes in project scope or timelines by adjusting the size and composition of your outstaffed teams without the long-term commitments that come with in-house hiring.
Moreover, outstaffing providers often have a roster of pre-vetted professionals ready to start, significantly reducing the time it takes to onboard new talent.
Outstaffing also allows you to avoid the risk of overhiring, which can lead to layoffs and financial strain during slower periods. Teams can be adjusted based on project requirements without long-term commitments.
5. Simplified HR and payroll
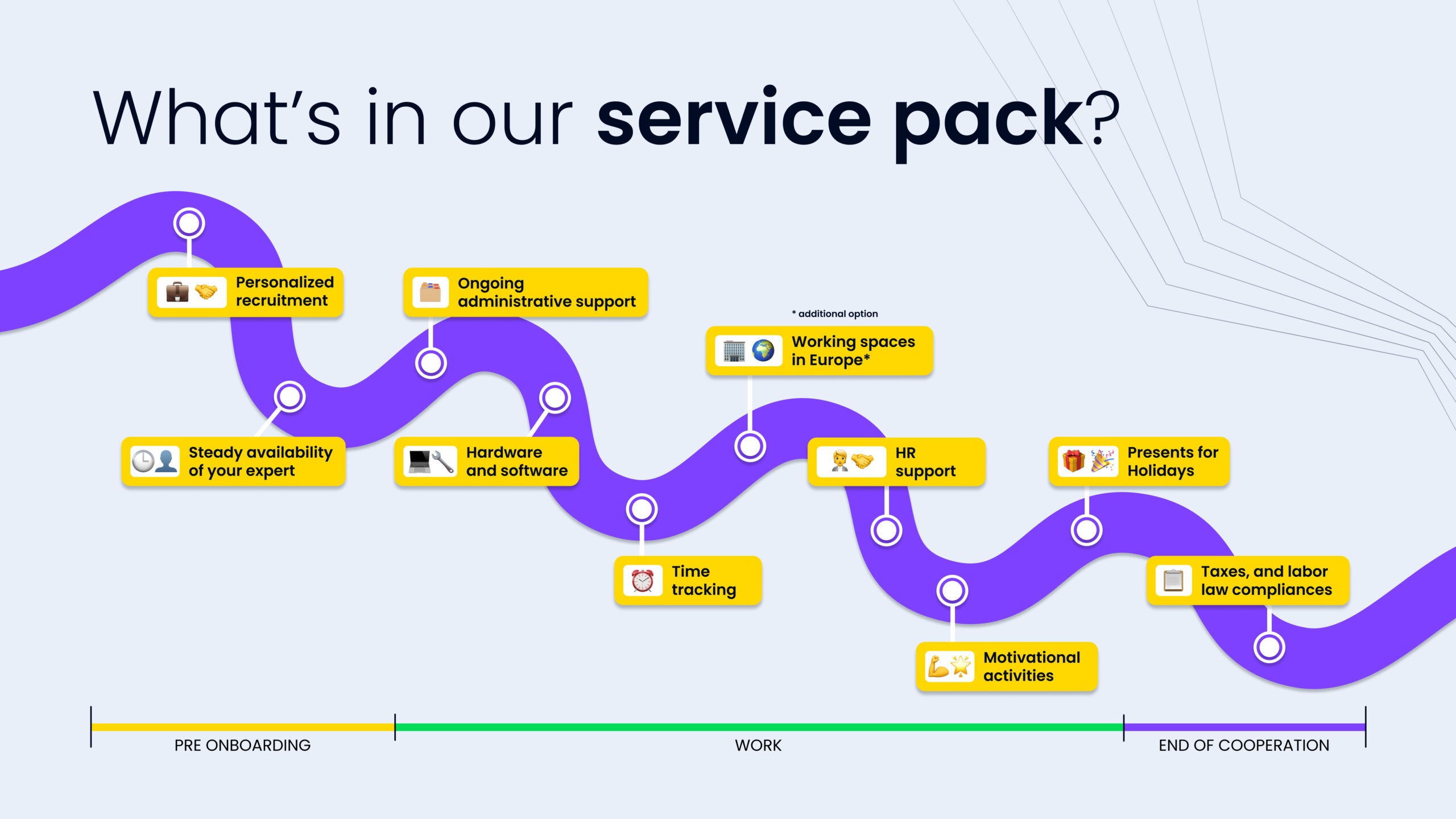
Outstaffing companies handle all HR functions, including recruitment, payroll, benefits, and compliance with local labor laws, freeing up in-house HR resources to focus on strategic initiatives.
Great staff augmentation vendors also manage legal and tax compliance, particularly when dealing with international teams, reducing the risk and complexity for the hiring company.
For example, here’s what you will find in the MWDN service pack:
Outstaffing partners share responsibility for the performance of the team, reducing the risk for the hiring company. If an outstaffed team member is not performing as expected, the provider can quickly replace them.
What’s more, outstaffed teams are typically more focused on deliverables and outcomes since their performance is directly tied to the success of the project. This can lead to higher efficiency and productivity compared to in-house teams, where distractions and competing priorities may affect focus.
How do you keep your data safe when working with third-party vendors?
We talked to MWDNers employed by cybersecurity companies or those who deal with sensitive information in other projects to find out what their companies (our clients) do to ensure their outstaffed team (MWDNers) is as secure as their in-house employees.
Ivan Protchenko (Twingate)
The work computer is used solely for professional purposes. Twingate, our zero-trust security tool, offers a more focused approach than a traditional VPN. It restricts access to only those company resources for which the employee has explicit permissions rather than allowing unrestricted access to all potential resources. Access is granted only to specific computers, not to any device from which the user might log in.
Password usage is minimized, with Single Sign-On (SSO) employed for most logins. All computers are managed through Mobile Device Management (MDM), enabling administrators to configure settings, ensure timely software updates, and remotely lock devices when needed.
Glib Sevruk (NDA)
Access to production servers requires a formal request process. Additionally, source code and Bitbucket test sites are protected by a VPN.
Olexii Lapuka (Twingate)

Everyone’s computer is equipped with Vanta and CrowdStrike. The primary restriction is the prohibition of portable storage devices. And of course, the company collects comprehensive information about the computer to ensure security.
Regarding leak prevention, this concern is typically more relevant for larger companies where personal connections are less common. In startups, effective monitoring and common sense generally suffice to address this issue.
Yevhenii Khlivetskyi (NDA)
On our projects, there are not so many cybersecurity tools or practices. First, the outstaffed team was invited to Slack as guests, meaning we only have access to specific channels. Second, we use a VPN service to access DEV servers during development.
Anton Lukashov (NDA)
We use VPNs, firewalls, and disk encryption to ensure security. Additionally, the company imposes fines for data breaches to reinforce the importance of protecting sensitive information.
Anton Shkurenko (Twingate)
Our security approach is straightforward:
- Minimal access. By default, no one has access to anything. Access is granted only when needed and kept to a minimum. Even our C-level managers don’t have direct access to many resources. If an account is hacked, the damage is limited.
- Frequent authentication. Access requires re-authentication every few hours through two services (soon to be three). It’s a bit annoying, but you get used to it.
- Regular secret rotation. We rotate secrets regularly, so even if something leaks, it won’t be valid for long.
- Encrypted data sharing. We never share anything that looks sensitive over chats or GitHub. Instead, we use secure services for sharing encrypted data, even for test passwords.
- Our own VPN. We use our own advanced VPN, which is part of our core product.
Something peculiar about MWDNers above
As a staff augmentation provider, we offer top-tier cybersecurity specialists to our clients. What’s even more impressive is that we also hire developers, QA engineers, DevOps, and other tech experts for companies creating their own cybersecurity products.
If you’re looking for a cost-effective way to build or enhance your cybersecurity solutions, we have skilled, pre-vetted professionals ready to support you.
Here are some other cybersecurity tools and methods you can use
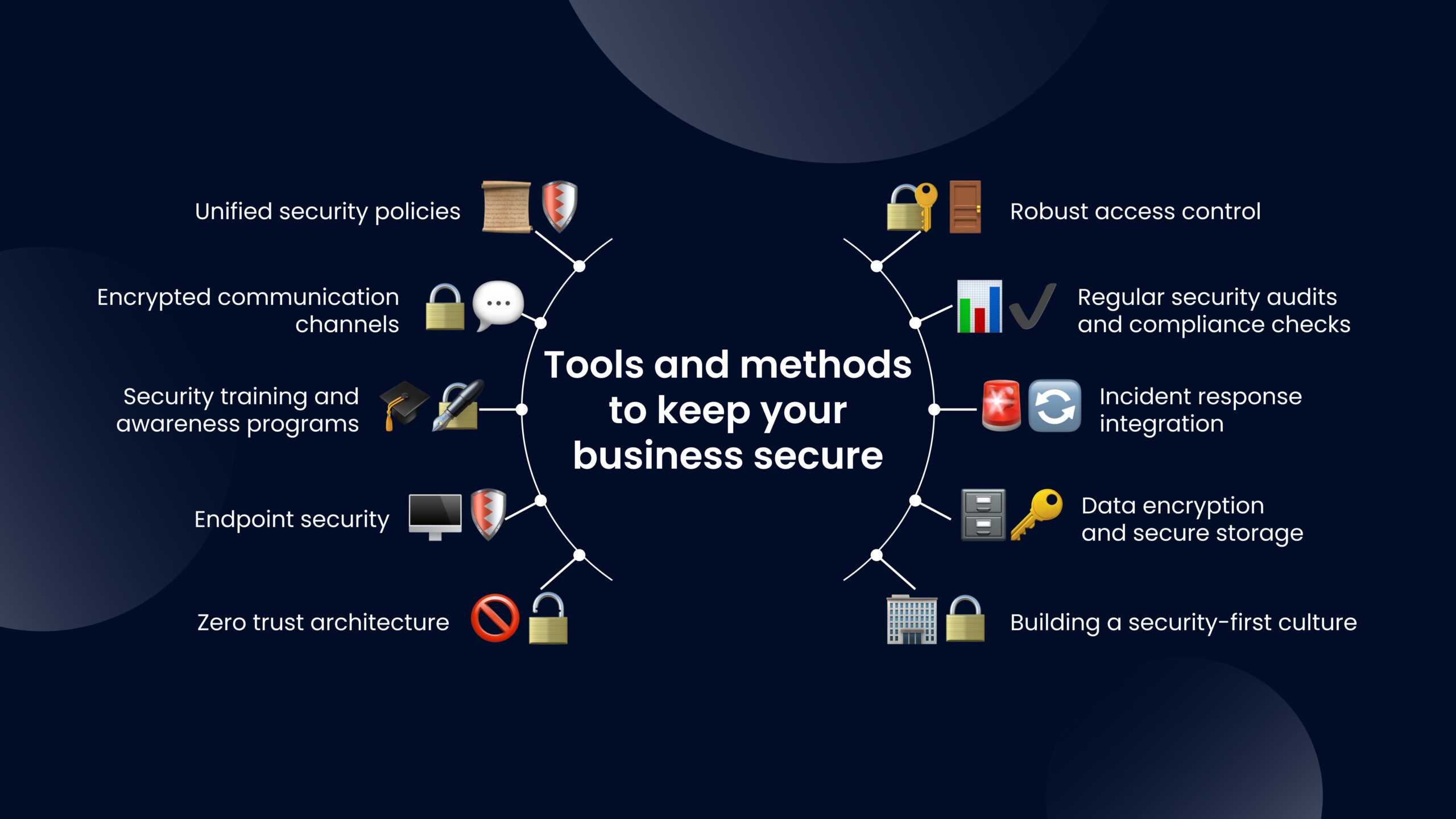
- Unified security policies. To maintain a consistent security posture, ensure that all security policies apply equally to outstaffed and in-house teams. This involves creating and enforcing standardized security protocols, including access controls, data protection measures, and incident response procedures. Everyone, regardless of their location, must adhere to the same rules, ensuring no weak links in the security chain.
- Robust access control. Implementing role-based access controls (RBAC) ensures that in-house and outstaffed employees only have access to the data and systems they need for their roles. This minimizes the risk of unauthorized access and ensures that sensitive information remains protected. Additionally, multi-factor authentication (MFA) should be used for all employees to add an extra layer of security.
- Encrypted communication channels. Ensure that all communication between in-house and outstaffed teams is encrypted. Whether it’s emails, instant messaging, or video conferences, using end-to-end encryption tools like Signal, encrypted email platforms, and secure video conferencing solutions helps protect sensitive information from eavesdropping.
- Regular security audits and compliance checks. Conduct regular security audits and compliance checks for both in-house and outstaffed teams. These audits help identify potential vulnerabilities and ensure that all employees, regardless of their location, are following security best practices.
- Security training and awareness programs. Security is not just about technology; it’s more about people. Provide ongoing security training and awareness programs to both in-house and outstaffed teams. These programs educate employees on the latest threats, such as phishing and social engineering, and teach them how to recognize and respond to them.
- Incident response integration. Integrate the outstaffed team into the company’s incident response plan. Ensure that outstaffed employees know how to report security incidents, participate in regular incident response drills, and have clear communication channels for escalating issues.
- Endpoint security. Invest in endpoint security solutions that protect your remote employees’ devices from malware, ransomware, and other cyber threats. Deploy antivirus software, firewalls, and secure VPNs on all outstaffed team members’ devices. Regular updates and patches should be applied automatically to ensure these devices are always protected against the latest threats.
- Data encryption and secure storage. Ensure that all sensitive data accessed or handled by outstaffed teams is encrypted in transit and at rest. Doing so will prevent unauthorized access even if the data is intercepted or compromised. Secure storage solutions, such as encrypted cloud storage, should be used to store sensitive information, with strict data access controls to limit who can view or modify this data.
- Zero trust architecture. Adopting a zero-trust security model helps protect the company’s assets by assuming that every user, device, and application—whether inside or outside the network—could be compromised. Strict verification processes, continuous monitoring of all activities, and limiting access based on real-time analysis ensure that security is maintained at all times, even if an outstaffed team member’s credentials are compromised.
- Building a security-first culture. Embed security into the company’s culture. Regular communication about the importance of security, recognition of employees who demonstrate strong security practices, and leadership by example all contribute to creating a security-first mindset. When both in-house and outstaffed employees see security as part of their daily responsibilities, it naturally becomes a shared priority.
So, the risks exist both for the in-house and outstaffed teams. There are tools you have to use and steps you must take to minimize these risks. You can also conduct verification both for your in-house and outstaffed teammates. However, the result is that these two approaches to business are equally safe and equally risky.
And you know what’s more? Your fear of staff augmentation for your business’s cybersecurity functions might be irrational.
Your fears are irrational – here’s why
The fear of choosing staff augmentation for cybersecurity functions is irrational, and this can be illustrated using the famous Monty Hall problem—a probability puzzle that demonstrates how our intuitions about risk can often be misleading.
The Monty Hall problem: A quick recap
In the Monty Hall problem, you are on a game show with three doors. Behind one door is a car (the prize you want), and behind the other two doors are goats (which you don’t want). You choose one door, say Door 1. The host, who knows what is behind each door, then opens another door, say Door 3, revealing a goat. Now, the host offers you a choice: stick with your original door (Door 1) or switch to the remaining unopened door (Door 2).

The counterintuitive answer
Intuitively, many people think that it doesn’t matter whether they switch or stay because there appear to be two doors left, each with a 50% chance of hiding the car. However, mathematically, you’re twice as likely to win the car if you switch doors. Initially, the chance that you chose the car was 1/3, and the chance that the car was behind one of the other two doors was 2/3. When the host opens one of the doors to reveal a goat, the 2/3 probability doesn’t split between the remaining doors; it stays with the unopened door. Therefore, switching doors gives you a 2/3 chance of winning, while sticking with your original choice only gives you a 1/3 chance.
Applying the Monty Hall problem to outstaffing cybersecurity
Let’s apply this logic to the fear of outstaffing cybersecurity. Many companies fear that outstaffing will expose them to greater risks because they’re handing over control of their sensitive data to an external party. This fear can be compared to the instinct to stick with the initial door in the Monty Hall problem—an intuitive, but ultimately flawed, decision.
- Sticking with in-house teams (staying with Door 1). Companies might think that keeping cybersecurity in-house ensures better control and security, much like a contestant might think sticking with the first chosen door is safer. However, in-house teams often lack the specialized knowledge, resources, or focus to handle complex cybersecurity threats effectively, making them more vulnerable to breaches (analogous to the lower 1/3 chance of winning by sticking with Door 1).
- Outstaffing cybersecurity (switching to Door 2). Augmenting your cybersecurity staff with a reliable vendor is like switching doors. The specialized vendor offers lower expenses, more experience hiring cybersecurity specialists, and a focused mission to protect your data. This means they are better equipped to manage threats and vulnerabilities, increasing your chances of staying secure (similar to the higher 2/3 chance of winning if you switch doors).
The irrational fear
Just as switching doors in the Monty Hall problem feels counterintuitive, it might feel counterintuitive to trust an external party with something as crucial as cybersecurity. But just as switching doors gives you a better chance of winning, outstaffing cybersecurity to a specialized provider often gives your company a better chance of staying secure. The fear is rooted in a misunderstanding of risk, similar to how people misunderstand the probabilities in the Monty Hall problem.
By outstaffing cybersecurity, you are not increasing your risk; you are strategically improving your security posture by leveraging the expertise and resources of specialized vendors. The irrational fear of outsourcing is like the irrational fear of switching doors in the Monty Hall problem—both are based on a misunderstanding of how to manage risk best.
MWDN – your reliable cybersecurity partner
At MWDN, we excel in identifying and hiring top cybersecurity experts from around the world, thoroughly vetting their reliability, and ensuring they are a strong cultural fit for your project. With years of experience in IT recruitment and tech talent administration, we bring deep expertise and adhere to the industry’s best practices to safeguard your project.
Beyond this, we offer all the advantages of staff augmentation, allowing you to strengthen your cybersecurity without introducing additional risks. With MWDN, you gain all the benefits of outstaffing, with the confidence that your project remains secure.