
FinTech is a combination of two words: “Finance” and “Technology.” It refers to software, apps, and other technologies that improve and automate financial services for individuals and businesses. Think of it as using technology to make money management easier and more efficient.
FinTech examples
Fintech encompasses a wide range of applications and services that are reshaping the financial industry. Here are several examples to make the notion clearer:
Payment systems
- Mobile payments. Using smartphones for transactions (e.g., Apple Pay, Google Pay).
- Peer-to-peer payments. Transferring money between individuals (e.g., Venmo, Zelle).
- Cryptocurrencies. Digital currencies operating on blockchain
Blockchain technology is a decentralized digital ledger that records transactions across many computers so that the registered transactions cannot be altered retroactively. This technology is the backbone of cryptocurrencies, but its applications extend far beyond just serving as the infrastructure for digital currencies.
Content:
Key concepts of blockchain
Applications beyond cryptocurrency
How does blockchain impact the IT sphere?
What are the possible future and challenges of blockchain technology?
Summing up
Below is a breakdown of the basic concepts, applications beyond cryptocurrency, and its impact on the IT industry.
Key concepts of blockchain
Decentralization. Unlike traditional centralized systems, blockchain operates on a distributed network of computers (nodes), eliminating a single point of control and failure.
Transparency. All transactions on the blockchain are visible to participants, ensuring transparency while maintaining privacy through cryptographic techniques.
Immutability. Once a transaction is recorded on the blockchain, it cannot be altered or deleted, guaranteeing the integrity of the transaction history.
Consensus mechanisms. Blockchain employs various consensus methods (e.g., Proof of Work, Proof of Stake) to validate transactions, ensuring all participants agree on the ledger's state without needing a trusted third party.
Applications beyond cryptocurrency
Blockchain's potential extends far beyond cryptocurrencies like Bitcoin and Ethereum. Where else can it become a game changer?
In supply chain management. Blockchain improves transparency and traceability in supply chains, enabling more efficient tracking of goods and authentication of product authenticity.
In smart contracts. Self-executing contracts with the terms directly written into code, automating and enforcing agreements without intermediaries, applicable in finance, real estate, and legal processes.
In healthcare. Secure and immutable records can enhance patient data management, ensuring privacy and enabling more efficient and accurate treatment and research.
In identity verification. Blockchain can offer a secure and unforgeable means of managing digital identities, applicable in voting systems, online authentication, and more.
In decentralized finance. Beyond traditional cryptocurrencies, blockchain supports the development of DeFi platforms, offering financial services without central financial intermediaries.
How does blockchain impact the IT sphere?
Blockchain introduces a new data management, security, and collaboration paradigm, massively affecting the whole IT sphere. Here are the trends we see in 2024:
1. Enhanced security and trust
Blockchain enhances data security and integrity through its decentralized nature and cryptographic hash functions. It provides a tamper-proof system where modifications to the data are virtually impossible without consensus, significantly reducing the risk of fraud and cyber-attacks. This has led IT sectors to adopt blockchain for secure transactions, data management, and identity verification, fostering trust in digital interactions.
2. Shift in skill sets and job opportunities
The rise of blockchain technology has created a demand for professionals with specialized skills in blockchain development, smart contract programming, and blockchain system design. This demand extends beyond technical roles to include legal, regulatory, and business strategy positions focused on blockchain applications. IT professionals are now seeking education and certification in blockchain technology to meet the growing need for expertise in this field.
3. Decentralization of applications and services
Blockchain enables the development of decentralized applications that operate on a peer-to-peer network rather than being controlled by a single entity. This shift challenges traditional centralized IT architectures and business models, prompting companies to explore decentralized solutions for enhanced transparency, security, and efficiency.
4. Innovation in infrastructure
The deployment and management of blockchain applications require new types of IT infrastructure, including distributed computing resources, specialized storage solutions, and enhanced network capabilities. This has led to innovation in cloud services, edge computing, and other IT infrastructure technologies to support the scalability, performance, and security needs of blockchain systems.
5. Regulatory and compliance challenges
As blockchain technology becomes more prevalent, IT departments must navigate an evolving regulatory landscape. Compliance with data protection regulations, understanding the legal implications of smart contracts, and managing cross-border data flows in a decentralized network are complex challenges that IT professionals must address.
6. Emergence of new business models
Blockchain technology supports new business models and revenue streams, such as tokenization, DeFi, and blockchain-as-a-service offerings. IT companies are exploring these models to provide innovative services to their customers, requiring shifts in business strategy, service delivery, and customer support.
7. Data management and interoperability
Blockchain offers new ways to manage and share data across organizations and systems securely. This potential for enhanced interoperability and data exchange is driving IT initiatives to leverage blockchain for supply chain management, healthcare records, and cross-industry data platforms.
What are the possible future and challenges of blockchain technology?
The future of blockchain technology is promising, yet it faces challenges that need to be addressed. Here’s a look at the prospective future developments and the hurdles blockchain technology faces.
Possible future of blockchain technology
Widespread adoption. Beyond finance and cryptocurrencies, blockchain is poised to revolutionize supply chain management, healthcare, real estate, and even government operations by providing transparent, secure, and efficient ways to record transactions and manage data.
Integration with other technologies. Blockchain is expected to increasingly integrate with other emerging technologies, such as IoT and AI, creating more secure and efficient systems for data exchange and automation.
Advancement in DeFi and DAOs. The finance sector may see a shift towards more decentralized platforms, reducing reliance on traditional financial institutions and promoting financial inclusion. DAOs could redefine organizational structures, with blockchain enabling truly decentralized and democratic decision-making processes.
Enhanced privacy and security features. Ongoing developments in blockchain technology will likely produce more sophisticated privacy-preserving technologies, enabling transactions and data management with enhanced security and anonymity.
Regulatory evolution and standardization. As blockchain becomes more mainstream, regulatory frameworks worldwide will evolve to better accommodate and facilitate its growth, including standards for interoperability, security, and privacy.
Challenges facing blockchain technology
Scalability issues. One of the major challenges blockchain faces is scalability. Many blockchain networks struggle to process transactions at scale, which is crucial for widespread adoption.
Energy consumption. Particularly for blockchains that use PoW consensus mechanisms, the energy consumption is significant, raising environmental concerns. There is a growing push towards more energy-efficient consensus mechanisms like PoS.
Regulatory and legal hurdles. The decentralized nature of blockchain poses regulatory challenges, including issues related to compliance with existing financial regulations, data privacy laws, and cross-border transactions.
Interoperability. As more blockchain networks emerge, the need for interoperability between different blockchains becomes critical to enable seamless exchange of information and value.
Public perception and understanding. Misunderstandings and the complex nature of blockchain technology can hinder its adoption. Clearer communication and educational efforts are needed to improve public perception and understanding.
Summing up
While blockchain technology holds transformative potential for numerous sectors, realizing this potential depends on overcoming technical, regulatory, and societal challenges. The future will likely see a combination of technological advancements, regulatory adjustments, and broader cultural shifts as blockchain technology matures and becomes more integrated into everyday business and society.
technology (e.g., Bitcoin, Ethereum).
Lending and borrowing
- Crowdfunding. Raising funds from a large number of people (e.g., Kickstarter, Indiegogo).
- Peer-to-peer lending. Connecting borrowers and lenders directly (e.g., Prosper, LendingClub).
- Digital wallets. Storing and managing digital payments (e.g., PayPal, Alipay).
Investment and wealth management
- Robo-advisors. Automated investment platforms (e.g., Betterment, Wealthfront).
- Crowdfunding platforms. Investing in startups and projects (e.g., Kickstarter, Indiegogo).
- Cryptocurrency exchanges. Platforms for trading cryptocurrencies (e.g., Coinbase, Binance).
Financial management
- Personal finance apps. Budgeting, saving, and tracking expenses (e.g., Mint, YNAB).
- InsurTech. Using technology to improve insurance services (e.g., Lemonade, Coverage).
FinTech is one of our favorite domains! MWDN has been hiring specialists for FinTech projects for many years. Today, our portfolio includes some well-known cases like VatBox, an app to manage your taxes, and Charge, a popular wallet with benefits.
How does a FinTech app work?
Let’s get to know how FinTech works with the example of a banking app. A banking app typically functions by connecting to a user’s bank account through secure APIs. This allows the app to access account information, initiate transactions, and provide various financial services.
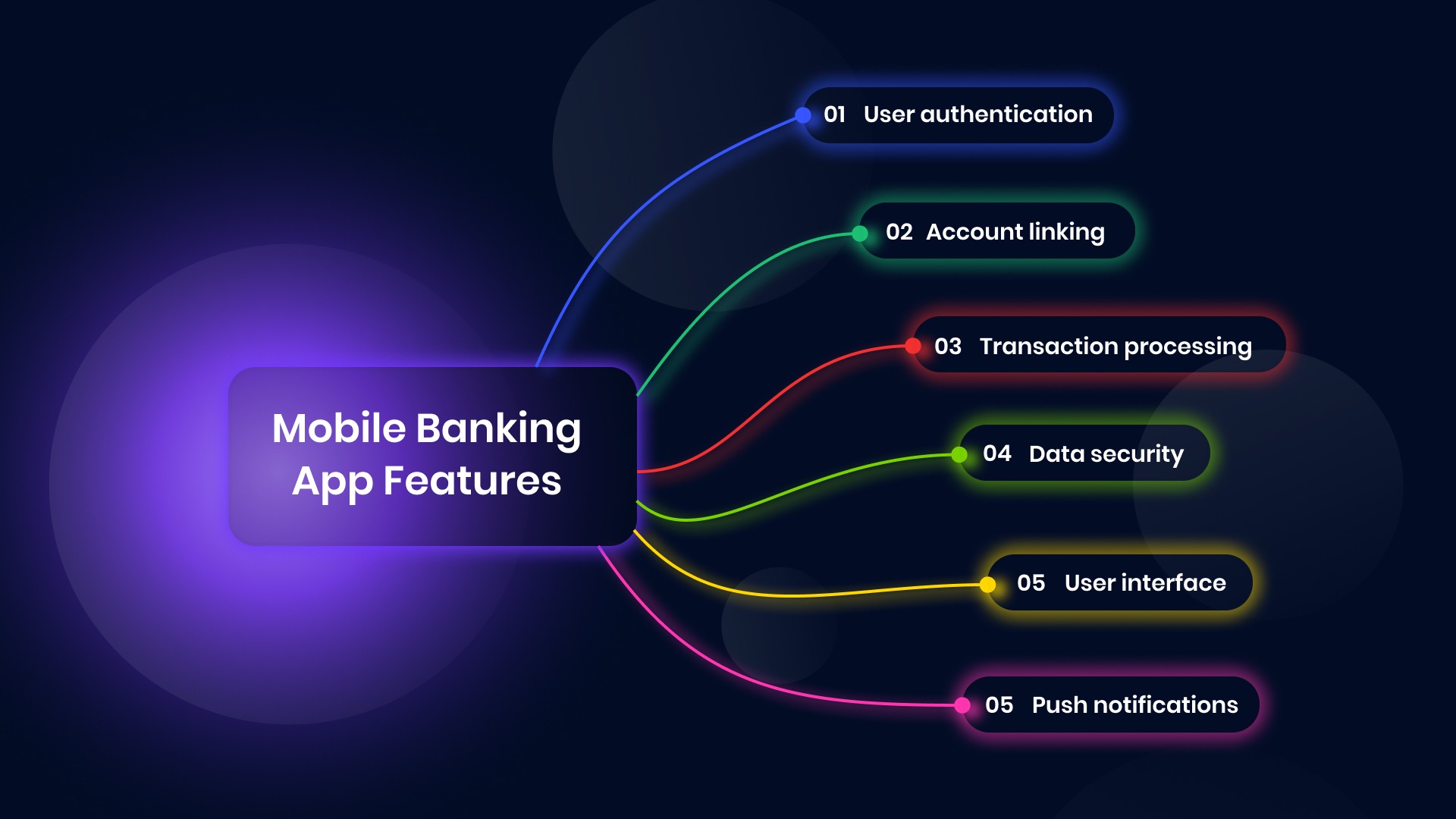
These are some of the key components and processes involved in the work of a FinTech banking app:
- User authentication. Strong security measures are essential to protect user data. This often involves multi-factor authentication (MFA) like fingerprint or facial recognition.
- Account linking. Users connect their bank accounts to the app using secure APIs provided by financial institutions.
- Transaction processing. The app facilitates fund transfers, bill payments, and other transactions through secure connections to the user’s bank.
- Data security. Robust encryption and security protocols are implemented to protect sensitive financial data.
- User interface. A user-friendly interface allows customers to easily navigate and perform various financial tasks.
- Push notifications. Real-time alerts for transactions, low balances, or other important notifications.
Additional features may include budgeting tools, investment options, and other financial management features.
What technologies are used in FinTech projects?
Fintech is a technology-driven industry that leverages various tools and platforms. Its core technologies include blockchain, which underpins cryptocurrencies and provides secure, transparent, and decentralized transaction recording; AI and ML, which are used for fraud detection, risk assessment, algorithmic trading, and personalized financial advice; cloud computing
Cloud computing is the delivery of computing services, including servers, storage, databases, networking, software, analytics, and more, over the internet (the cloud) to offer faster innovation, flexible resources, and economies of scale. Cloud computing enables users to access and utilize various IT resources and services on demand without needing to own or manage physical hardware or infrastructure.
Five key characteristics of cloud computing
On-demand self-service. Users can provision and manage computing resources as needed, often through a self-service portal, without requiring human intervention from the service provider.
Broad network access. Cloud services are accessible over the internet from a wide range of devices, including laptops, smartphones, tablets, and desktop computers.
Resource pooling. Cloud providers pool and allocate resources dynamically to multiple customers. Resources are shared among users but are logically segmented and isolated.
Rapid elasticity. Cloud resources can be rapidly scaled up or down to accommodate changes in demand. This scalability ensures that users can access the resources they need without overprovisioning or underutilization.
Measured service. Cloud usage is often metered and billed based on actual usage, allowing users to pay for only the resources they consume. This "pay-as-you-go" model offers cost efficiency and flexibility.
Service models of cloud computing
There are three primary service models of cloud computing: IaaS, PaaS, and SaaS. Let’s break them down.
IaaS
Infrastructure as a Service provides virtualized computing resources over the internet. Users can access virtual machines, storage, and networking components, allowing them to deploy and manage their software applications and services.
Description: IaaS provides users with virtualized computing resources over the internet. These resources typically include virtual machines, storage, and networking components. Users can provision and manage these resources on demand, giving them control over the underlying infrastructure.
Use Cases: IaaS is suitable for users who need flexibility and control over their computing environment. It's commonly used for hosting virtual servers, running applications, and managing data storage.
Examples: Amazon Web Services (AWS) EC2, Microsoft Azure Virtual Machines, Google Cloud Compute Engine.
PaaS
Platform as a Service offers a higher-level development and deployment environment. It includes tools and services for building, testing, deploying, and managing applications. Developers can focus on writing code while the platform handles infrastructure management.
Description: PaaS offers a higher-level development and deployment environment that abstracts much of the underlying infrastructure complexity. It includes tools, services, and development frameworks that enable users to build, test, deploy, and manage applications without worrying about the infrastructure.
Use Cases: PaaS is ideal for developers who want to focus solely on coding and application logic without managing servers or infrastructure. It accelerates application development and deployment.
Examples: Heroku, Google App Engine, and Microsoft Azure App Service.
SaaS
Software as a Service delivers fully functional software applications over the internet. Users can access and use software applications hosted in the cloud without the need for installation or maintenance. Common examples include email services, customer relationship management (CRM) software, and office productivity suites.
Description: SaaS delivers fully functional software applications over the internet. Users can access and use these applications through a web browser without the need for installation or maintenance. SaaS providers handle everything from infrastructure management to software updates.
Use Cases: SaaS is widely used for various business applications, including email, collaboration tools, customer relationship management (CRM), human resources management, and more.
Examples: Salesforce, Microsoft 365 (formerly Office 365), Google Workspace, Dropbox.
These three cloud computing service models represent a spectrum of offerings, with IaaS providing the most control over infrastructure and SaaS offering the highest level of abstraction and simplicity for end-users. Organizations can choose the service model that best aligns with their specific needs, resources, and expertise.
How are cloud services hosted and delivered?
Public Cloud. Services are offered to the general public by cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). Resources are shared among multiple customers.
Private Cloud. Cloud infrastructure is exclusively used by a single organization. It can be hosted on-premises or by a third-party provider. Private clouds offer more control and customization options.
Hybrid Cloud. A combination of public and private clouds, allowing data and applications to be shared between them. Hybrid clouds provide flexibility, enabling organizations to leverage the scalability of public clouds while maintaining sensitive data on private infrastructure.
Multi-Cloud. Companies use services from multiple cloud providers to avoid vendor lock-in and exploit each provider's strengths. Multi-cloud strategies often involve managing resources and applications across various cloud environments.
Cloud computing providers
These are some of the most popular and widely recognized cloud computing providers.
Amazon Web Services (AWS)
AWS is one of the largest and most widely used cloud service providers globally. It offers a vast array of cloud services, including computing, storage, databases, machine learning, and analytics
Notable services: Amazon EC2 (Elastic Compute Cloud), Amazon S3 (Simple Storage Service), AWS Lambda, Amazon RDS (Relational Database Service).
Website: AWS
Microsoft Azure
Azure is Microsoft's cloud computing platform, providing a comprehensive suite of cloud services, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
Notable services: Azure Virtual Machines, Azure App Service, Azure SQL Database, Azure AI and Machine Learning.
Website: Microsoft Azure
Google Cloud Platform (GCP)
GCP offers cloud services for computing, data storage, machine learning, and data analytics. Google's expertise in data and AI is a standout feature of GCP.
Notable services: Google Compute Engine, Google Kubernetes Engine (GKE), BigQuery, Google Cloud AI Platform.
Website: Google Cloud
IBM Cloud
IBM Cloud provides cloud computing and AI services with a focus on hybrid and multi-cloud solutions. It offers a variety of cloud deployment options, including public, private, and on-premises.
Notable services: IBM Virtual Servers, Watson AI services, IBM Cloud Object Storage, Red Hat OpenShift on IBM Cloud.
Website: IBM Cloud
Oracle Cloud
Oracle Cloud offers cloud infrastructure and services, including databases, applications, and cloud-native technologies. It is designed to support enterprise workloads and applications.
Notable services: Oracle Cloud Infrastructure (OCI), Oracle Autonomous Database, Oracle Cloud Applications.
Website: Oracle Cloud
Alibaba Cloud
Alibaba Cloud is a leading cloud service provider in Asia and offers a wide range of cloud computing services, data storage, and AI capabilities.
Notable services: Elastic Compute Service (ECS), Alibaba Cloud Object Storage Service (OSS), Alibaba Cloud Machine Learning Platform.
Website: Alibaba Cloud
Salesforce (Heroku)
Salesforce provides a cloud-based platform known for its CRM solutions. Heroku, a subsidiary of Salesforce, is a cloud platform for building, deploying, and managing applications.
Notable services: Salesforce CRM, Heroku Platform as a Service (PaaS).
Website: Salesforce, Heroku
, which provides scalable infrastructure for fintech applications; big data
Big data is a massive amount of information that is too large and complex for traditional data-processing application software to handle. Think of it as a constantly flowing firehose of data, and you need special tools to manage and understand it.
Big data definition in simple words
Big data encompasses structured, unstructured, and semi-structured data that grows exponentially over time. It can be analyzed to uncover valuable insights and inform strategic decision-making.
The term often describes data sets characterized by the "three Vs": Volume (large amounts of data), Velocity (rapidly generated data), and Variety (diverse data types).
How does big data work?
Big data is processed through a series of stages.
Data generation → Data is produced from sources, including social media, sensors, transactions, and more.
Data capture → This involves collecting data and storing it in raw format.
Data storage → Data is stored in specialized data warehouses or data lakes designed to handle massive volumes.
Data processing → Raw data is cleaned, transformed, and structured to make it suitable for analysis.
Data analysis → Advanced analytics tools and techniques, like machine learning and artificial intelligence, are applied to extract valuable insights and patterns.
Data visualization → Results are presented in visual formats like graphs, charts, and dashboards for easy interpretation.
What are the key technologies used in big data processing?
Big data processing relies on a combination of software and hardware technologies. Here are some of the most prominent ones.
Data storage
Hadoop Distributed File System (HDFS). Stores massive amounts of data across multiple nodes in a distributed cluster.
NoSQL databases. Designed for handling unstructured and semi-structured data, offering flexibility and scalability.
Data processing
Apache Hadoop. A framework for processing large datasets across clusters of computers using parallel processing.
Apache Spark. A fast and general-purpose cluster computing framework for big data processing.
MapReduce. A programming model for processing large data sets with parallel and distributed algorithms.
Data analysis
SQL and NoSQL databases. For structured and unstructured data querying and analysis.
Data mining tools. For discovering patterns and relationships within large data sets.
Machine learning and AI. For building predictive models and making data-driven decisions.
Business intelligence tools. For data visualization and reporting.
What is the practical use of big data?
Big data has revolutionized the way businesses operate and make decisions. In business, it helps with customer analytics, marketing optimization, fraud detection, supply chain management, and risk management. But that’s not all!
Big data in healthcare
Analyzing data helps identify potential disease outbreaks and develop prevention strategies. It became an important tool for virologists and immunologists, who use data to predict not only when and what kind of disease can outbreak, but also the exact stamm of a virus or an infection.
Big data helps create personalized medicine by tailoring treatments based on individual patient data. It also accelerates the drug development process by analyzing vast amounts of biomedical data.
Big data for the government
Big data can help create smart cities by optimizing urban planning, traffic management, and resource allocation. It can help the police to analyze crime patterns and improve policing strategies and response times. For disaster-prone regions, big data can help predict and respond to natural disasters.
Essentially, big data has the potential to transform any industry by providing insights that drive innovation, efficiency, and decision-making. That includes
finance (fraud detection, risk assessment, algorithmic trading),
manufacturing (predictive maintenance, quality control, supply chain optimization),
energy (smart grids, energy efficiency, demand forecasting), and even
agriculture (precision agriculture, crop yield prediction, and resource optimization).
What kinds of specialists work with big data?
The world of big data requires a diverse range of professionals to manage and extract value from complex datasets. Among the core roles are Data Engineers, Data Scientists, and Data Analysts. While these roles often intersect and collaborate, they have distinct responsibilities within big data.
Data engineers focus on building and maintaining the infrastructure that supports data processing and analysis. Their responsibilities include:
Designing and constructing data pipelines.
Developing and maintaining data warehouses and data lakes.
Ensuring data quality and consistency.
Optimizing data processing for performance and efficiency.
They usually need strong programming skills (Python, Java, Scala) and be able to work with database management, cloud computing (AWS, GCP, Azure), data warehousing, and big data tools (Hadoop, Spark).
A data analyst’s focus is on extracting insights from data to inform business decisions. Here’s exactly what they’re responsible for:
Collecting, cleaning, and preparing data for analysis.
Performing statistical analysis and data mining.
Creating visualizations and reports to communicate findings.
Collaborating with stakeholders to understand business needs.
Data analysts should be pros in SQL, data visualization tools (Tableau, Power BI), and statistical software (R, Python).
Data scientists apply advanced statistical and machine-learning techniques to solve complex business problems. They do so by:
Building predictive models and algorithms.
Developing machine learning pipelines.
Experimenting with new data sources and techniques.
Communicating findings to technical and non-technical audiences.
Data scientists need strong programming skills (Python, R), knowledge of statistics, machine learning, and data mining, and a deep understanding of business problems.
In essence, Data Engineers build the foundation for data analysis by creating and maintaining the data infrastructure. Data Analysts focus on exploring and understanding data to uncover insights, while Data Scientists build predictive models and algorithms to solve complex business problems. These roles often work collaboratively to extract maximum value from data.
Along with this trio, there are also other supporting roles. A Data Architect will design the overall architecture for big data solutions. A Database Administrator will manage and maintain databases. A Data Warehouse Architect will design and implement data warehouses. A Business Analyst will translate business needs into data requirements. These roles often overlap and require a combination of technical and business skills. As the field evolves, new roles and specializations are also emerging.
What is the future of big data?
The future of big data is marked by exponential growth and increasing sophistication. These are just some of the trends we should expect in 2024 and beyond.
Quantum computing promises to revolutionize big data processing by handling complex calculations at unprecedented speeds.
Processing data closer to its source will reduce latency and improve real-time insights.
AI and ML will become even more integrated into big data platforms, enabling more complex analysis and automation.
As data becomes more valuable, regulations like GDPR and CCPA will continue to shape how data is collected, stored, and used.
Responsible data practices, including bias detection and mitigation, will be crucial.
Turning data into revenue streams will become increasingly important.
The demand for skilled data scientists and analysts will continue to outpace supply.
Meanwhile, big data is not without its challenges. Ensuring its accuracy and consistency will remain a challenge and an opportunity for competitive advantage.
to processes vast amounts of financial data for insights and predictions, and cybersecurity
What is cybersecurity? Cybersecurity encompasses the techniques and processes aimed at protecting computer systems, networks, and data from digital threats, unauthorized access, or damage. It involves deploying security measures, including firewalls, antivirus software, and intrusion detection systems, coupled with user education and stringent security policies.
With hybrid wars that include cyber attacks today, the importance of cybersecurity, common threats, and best practices for protection is essential.
What does cybersecurity do?
Protecting sensitive data. Cybersecurity shields personal and corporate data from theft, damage, or unauthorized modification. According to Verizon's 2023 report, data breaches have increased by 33% over the past year, emphasizing the need for robust data protection.
Preventing unauthorized access. Cybersecurity practices involve implementing measures like multi-factor authentication and access controls. A study by IBM found that unauthorized access was a primary cause of 43% of data breaches.
Maintaining privacy. This function of cybersecurity is essential for safeguarding user data against illicit tracking and collection. Privacy laws like GDPR in the EU have put a spotlight on the importance of privacy in cybersecurity.
Ensuring continuity of business operations. Cybersecurity prevents disruptions caused by cyberattacks. For example, the WannaCry ransomware attack of 2017 caused an estimated $4 billion in worldwide losses.
Legal and regulatory compliance. Non-compliance with laws like HIPAA can lead to heavy fines. For example, HIPAA violations can cost up to $1.5 million per incident.
Building trust. Effective cybersecurity practices enhance customer confidence. Surveys indicate that 85% of consumers value privacy and data protection when choosing companies to do business with.
Cybersecurity is integral to modern business operations, offering protection against a wide range of digital threats and ensuring compliance with legal standards. It safeguards data and plays a vital role in maintaining business continuity and building customer trust.
Common cybersecurity threats
These are some of the most common threats modern companies have to face.
Malware encompasses various forms of harmful software, including viruses that can replicate themselves, worms that spread across networks, trojans that disguise themselves as legitimate software, and ransomware that locks users out of their systems until a ransom is paid. The impact of malware can be severe: for example, the WannaCry ransomware attack we mentioned above affected more than 200,000 computers across 150 countries.
Phishing attacks involve deceptive emails or websites that trick individuals into revealing sensitive information like passwords or credit card numbers. The FBI’s Internet Crime Report noted that phishing was the most common type of cybercrime in 2020.
Man-in-the-middle attacks (MitM). This form of eavesdropping intercepts communication between two parties to steal or alter the data. A common example is a hacker intercepting data on an unsecured Wi-Fi network.
Denial of service (DoS) attacks flood systems, servers, or networks with traffic to exhaust resources and bandwidth, rendering the service unusable. One of the most notorious DoS attacks was against Dyn, a major DNS provider, in 2016, disrupting internet platforms and services.
SQL injection involves inserting malicious code into SQL-using databases via a vulnerable website, which can then be used to access and manipulate confidential data. For example, in 2019, a SQL injection attack exposed the data of over 1 million customers of an Australian telecommunications company.
Zero-day exploits target unknown vulnerabilities in software or hardware, making them particularly dangerous as they occur before the vendor becomes aware and fixes the issue. The Stuxnet worm, discovered in 2010, is one of the most famous examples of a zero-day exploit.
Best practices for IT and cyber protection
Here are some things you can do as an individual or as a business owner to protect your personal and sensitive data from the simplest attacks and cyber threats.
1/ Strong passwords and multi-factor authentication. Strong, unique passwords, coupled with MFA, significantly heighten security. According to Verizon's Data Breach Investigations Report, 81% of hacking-related breaches leveraged either stolen and/or weak passwords.
2/ Regular software updates. Consistently updating software and systems helps patch security vulnerabilities. Microsoft reported that updating systems could prevent 85% of targeted cyberattacks.
3/ Employee training and awareness. Training staff on cybersecurity risks is essential. IBM’s Cyber Security Intelligence Index found that 95% of cybersecurity breaches are due to human error.
4/ Firewalls and antivirus software. These tools are fundamental in safeguarding against various cyber threats. The use of antivirus software can detect and block nearly 100% of known malware.
5/ Data encryption. Encrypting sensitive data, both in transit and at rest, is critical. A study by the Ponemon Institute showed that encryption can significantly reduce the cost of a data breach.
6/ Regular backups. Backing up data ensures recovery in the event of an attack. Companies that regularly back up and encrypt their data can reduce the impact of data breaches significantly.
7/ Incident response plan. An effective response plan can reduce the cost of a data breach by as much as 40%, according to IBM’s Cost of a Data Breach report.
8/ Secure Wi-Fi networks. Securing wireless networks is vital. A survey by Symantec revealed that 60% of consumers believe their Wi-Fi networks are secure, but only 50% have taken steps to secure them.
9/ Vulnerability assessments and penetration testing. Regular testing and patching of vulnerabilities are key. Cisco’s Annual Cybersecurity Report highlighted that 42% of organizations faced public scrutiny after a security breach.
10/ Limiting user access. Implementing the principle of least privilege can significantly reduce risks. A study by Forrester found that 80% of security breaches involve privileged credentials.
What kind of specialists provide IT and cyber protection?
As cybersecurity is so complex and varied, it demands many skills from its providers. What used to be done by one person today is covered by five specialists and more. Here are some of the job positions you can find in cybersecurity and a short explanation of what these people do.
Cybersecurity Analyst monitors networks for security breaches, investigates violations, and implements protection solutions.
Network Security Engineer designs, implements, and maintains network security solutions to protect against cyber threats.
Information Security Manager oversees and coordinates the company’s information security policies and procedures.
Chief Information Security Officer (CISO) is a high-level executive responsible for the overall strategy and direction of information security in an organization.
Ethical Hacker/Penetration Tester simulates cyber attacks to identify and fix security vulnerabilities.
Security Software Developer develops security software, such as encryption technologies and firewall programs.
IT Security Consultant advises on best practices for protecting companies’ IT infrastructure and data.
to protects sensitive financial information from cyber threats.
Among the most popular programming languages and frameworks developers use to create FinTech apps are Python, which is popular for data analysis, machine learning
Machine learning (ML) is a subset of artificial intelligence (AI) that enables systems to learn and improve from experience without being explicitly programmed. It involves the development of algorithms that can analyze and learn from data, making decisions or predictions based on this data.
Common misconceptions about machine learning
ML is the same as AI. In reality, ML is a subset of AI. While AI is the broader concept of machines being able to carry out tasks in a way that we would consider “smart,” ML is a specific application of AI where machines can learn from data.
ML can learn and adapt on its own. In reality, ML models do learn from data, but they don't adapt or evolve autonomously. They operate and make predictions within the boundaries of their programming and the data they are trained on. Human intervention is often required to update or tweak models.
ML eliminates the need for human workers. In reality, while ML can automate certain tasks, it works best when complementing human skills and decision-making. It's a tool to enhance productivity and efficiency, not a replacement for the human workforce.
ML is only about building algorithms. In reality, algorithm design is a part of ML, but it also involves data preparation, feature selection, model training and testing, and deployment. It's a multi-faceted process that goes beyond just algorithms.
ML is infallible and unbiased. In reality, ML models can inherit biases present in the training data, leading to biased or flawed outcomes. Ensuring data quality and diversity is critical to minimize bias.
ML works with any kind of data. In reality, ML requires quality data. Garbage in, garbage out – if the input data is poor, the model's predictions will be unreliable. Data preprocessing is a vital step in ML.
ML models are always transparent and explainable. In reality, some complex models, like deep learning networks, can be "black boxes," making it hard to understand exactly how they arrive at a decision.
ML can make its own decisions. In reality, ML models can provide predictions or classifications based on data, but they don't "decide" in the human sense. They follow programmed instructions and cannot exercise judgment or understanding.
ML is only for tech companies. In reality, ML has applications across various industries – healthcare, finance, retail, manufacturing, and more. It's not limited to tech companies.
ML is a recent development. In reality, while ML has gained prominence recently due to technological advancements, its foundations were laid decades ago. The field has been evolving over a significant period.
Building blocks of machine learning
We can state that machine learning consists of certain blocks, like algorithms and data. What is their role exactly?
Algorithms are the rules or instructions followed by ML models to learn from data. They can be as simple as linear regression or as complex as deep learning neural networks. Some of the popular algorithms include:
Linear regression – used for predicting a continuous value.
Logistic regression – used for binary classification tasks (e.g., spam detection).
Decision trees – A model that makes decisions based on branching rules.
Random forest – An ensemble of decision trees typically used for classification problems.
Support vector machines – Effective in high dimensional spaces, used for classification and regression tasks.
Neural networks – A set of algorithms modeled after the human brain, used in deep learning for complex tasks like image and speech recognition.
K-means clustering – An unsupervised algorithm used to group data into clusters.
Gradient boosting machines – Builds models in a stage-wise fashion; it's a powerful technique for building predictive models.
An ML model is what you get when you train an algorithm with data. It's the output that can make predictions or decisions based on new input data. Different types of models include decision trees, support vector machines, and neural networks.
What’s the role of data in machine learning?
Data collection. The process of gathering information relevant to the problem you're trying to solve. This data can come from various sources and needs to be relevant and substantial enough to train models effectively.
Data processing. This involves cleaning and transforming the collected data into a format suitable for training ML models. It includes handling missing values, normalizing or scaling data, and encoding categorical variables.
Data usage. The processed data is then used for training, testing, and validating the ML models. Data is crucial in every step – from understanding the problem to fine-tuning the model for better accuracy.
Tools and technologies commonly used in ML
Python and R are the most popular due to their robust libraries and frameworks specifically designed for ML (like Scikit-learn, TensorFlow, and PyTorch for Python).
Data Analysis Tools: Pandas, NumPy, and Matplotlib in Python are essential for data manipulation and visualization.
Machine Learning Frameworks: TensorFlow, PyTorch, and Keras are widely used for building and training complex models, especially in deep learning.
Cloud Platforms: AWS, Google Cloud, and Azure offer ML services that provide scalable computing power and storage, along with various ML tools and APIs.
Big Data Technologies: Tools like Apache Hadoop and Spark are crucial when dealing with large datasets that are typical in ML applications.
Automated Machine Learning (AutoML): Platforms like Google's AutoML provide tools to automate the process of applying machine learning to real-world problems, making it more accessible.
Three types of ML
Machine Learning (ML) can be broadly categorized into three main types: Supervised learning, Unsupervised learning, and Reinforcement learning. Let's explore them with examples
Supervised learning
In supervised learning, the algorithm learns from labeled training data, helping to predict outcomes or classify data into groups. For example:
Email spam filtering. Classifying emails as “spam” or “not spam” based on distinguishing features in the data.
Credit scoring. Assessing credit worthiness of applicants by training on historical data where the credit score outcomes are known.
Medical diagnosis. Using patient data to predict the presence or absence of a disease.
Unsupervised learning
Unsupervised learning involves training on data without labeled outcomes. The algorithm tries to identify patterns and structures in the data. Real-world examples:
Market basket analysis. Identifying patterns in consumer purchasing by grouping products frequently bought together.
Social network analysis. Detecting communities or groups within a social network based on interactions or connections.
Anomaly detection in network traffic. Identifying unusual patterns that could signify network breaches or cyberattacks.
Reinforcement learning
Reinforcement learning is about taking suitable actions to maximize reward in a particular situation. It is employed by various software and machines to find the best possible behavior or path in a specific context. These are some examples:
Autonomous vehicles. Cars learn to drive by themselves through trial and error, with sensors providing feedback.
Robotics in manufacturing. Robots learn to perform tasks like assembling with increasing efficiency and precision.
Game AI. Algorithms that learn to play and improve at games like chess or Go by playing numerous games against themselves or other opponents.
How do we use ML in real life?
Predictive analytics is used in sales forecasting, risk assessment, and customer segmentation.
Customer service. Chatbots and virtual assistants powered by ML can handle customer inquiries efficiently.
Fraud detection. ML algorithms can analyze transaction patterns to identify and prevent fraudulent activities.
Supply chain optimization. Predictive models can forecast inventory needs and optimize supply chains.
Personalization. In marketing, ML can be used for personalized recommendations and targeted advertising.
Human resources. Automating candidate screening and using predictive models to identify potential successful hires.
Predicting patient outcomes in healthcare
Researchers at Beth Israel Deaconess Medical Center used ML to predict the mortality risk of patients in intensive care units. By analyzing medical data like vital signs, lab results, and notes, the ML model could predict patient outcomes with high accuracy.
This application of ML aids doctors in making critical treatment decisions and allocating resources more effectively, potentially saving lives.
Fraud detection in finance and banking
JPMorgan Chase implemented an ML system to detect fraudulent transactions. The system analyzes patterns in large datasets of transactions to identify potentially fraudulent activities.
The ML model helps in reducing financial losses due to fraud and enhances the security of customer transactions.
Personalized shopping experiences in retail
Amazon uses ML algorithms for its recommendation system, which suggests products to customers based on their browsing and purchasing history.
This personalized shopping experience increases customer satisfaction and loyalty, and also boosts sales by suggesting relevant products that customers are more likely to purchase.
Predictive maintenance in manufacturing
Airbus implemented ML algorithms to predict failures in aircraft components. By analyzing data from various sensors on planes, they can predict when parts need maintenance before they fail.
This approach minimizes downtime, reduces maintenance costs, and improves safety.
Precision farming in agriculture
John Deere uses ML to provide farmers with insights about planting, crop care, and harvesting, using data from field sensors and satellite imagery.
This information helps farmers make better decisions, leading to increased crop yields and more efficient farming practices.
Autonomous driving in automotive
Tesla's Autopilot system uses ML to enable semi-autonomous driving. The system processes data from cameras, radar, and sensors to make real-time driving decisions.
While still in development, this technology has the potential to reduce accidents, ease traffic congestion, and revolutionize transportation.
, and backend
The backend is like the kitchen. You don't see it, but it's where all the magic happens. The chefs prepare your food (process data), the kitchen staff manages ingredients (stores data), and the dishwasher cleans up (data management). The waiter (frontend) brings you the food (information), but the real work happens behind the scenes in the kitchen (backend).
Backend definition
Backend refers to the server-side of a software application or website, responsible for business logic, data management, and application functionality. It encompasses the underlying infrastructure and processes that support the user interface.
Backend components
The server is the backbone of a backend system. It's a powerful computer that handles requests from clients (like web browsers or mobile apps), processes them, and sends back responses. Imagine it as a receptionist directing visitors and providing information.
A database is where information is stored and organized. It's like a digital filing cabinet for the application. There are different types of databases (relational, NoSQL) to suit various data storage needs.
Application logic is the brain of the application. It defines how the application should respond to different inputs and requests. It's the set of rules and calculations that determine the output. For example, calculating the total cost of a shopping cart or verifying user login credentials.
API (Application Programming Interface) is a set of rules for building and interacting with software applications. It's like a contract defining how different parts of the system communicate. For example, a mobile app might use an API to fetch data from a backend server.
These components work together to create a functional backend system. The server handles requests, the database stores data, the application logic processes information, and the API facilitates communication between different parts of the system.
Backend processes examples
Backend processes encompass a wide range of activities that ensure the smooth functioning of a web application. Here are some examples:
User authentication and authorization
Verifying user credentials (username, password) against a database.
Generating and managing session tokens.
Enforcing access controls based on user roles and permissions.
Data management
Storing and retrieving user data (profiles, preferences, purchase history).
Managing product information, inventory, and pricing.
Processing transactions (payments, orders, refunds).
API management
Defining endpoints for accessing application data and functionalities.
Handling API requests and responses.
Implementing API security measures.
Error handling and logging
Detecting and handling exceptions to prevent application crashes.
Recording system events and errors for troubleshooting and analysis.
Performance optimization
Caching frequently accessed data.
Load balancing to distribute traffic across multiple servers.
Database query optimization.
Technologies used for backend development
Backend development involves using a combination of languages, frameworks, and databases to build an application's server-side logic.
Programming languages and frameworks
Python. Known for its readability and versatility, used extensively in web development, data science, and machine learning. Django is a high-level framework for rapid web development.
Java. A robust language for enterprise-level applications, offering strong typing and performance. Spring Boot simplifies Java-based application development.
JavaScript is primarily used for frontend development. However, Node.js enables building scalable backend applications and Express.js is a minimalist framework for Node.js.
Ruby. Emphasizes developer happiness and productivity, popularized by Ruby on Rails framework. Ruby on Rails provides a structured approach to building web applications.
PHP. Widely used for web development, known for its simplicity and ease of learning. Laravel is its most popular framework for building web applications.
C#. Often used in Microsoft-centric environments, offering strong typing and performance.
Databases
Relational Databases: Store data in structured tables (MySQL, PostgreSQL, SQL Server).
NoSQL Databases: Handle unstructured or semi-structured data (MongoDB, Cassandra, Redis).
The choice of technologies depends on factors like project requirements, team expertise, and performance needs.
Who are backend developers? What stack of skills should they have?
Backend developers are the unsung heroes of the digital world, responsible for the technical infrastructure that powers websites and applications. They focus on the server-side logic, handling data management, and ensuring seamless application performance. Backend developers often collaborate with frontend developers, database administrators, and DevOps engineers to create robust and scalable applications.
Essential skill set
To excel in backend development, devs usually have a strong foundation in:
Languages: Python, Java, JavaScript (Node.js), Ruby, PHP, or C#.
Databases: Relational databases (MySQL, PostgreSQL, SQL Server) and NoSQL databases (MongoDB, Cassandra).
Server-side frameworks: Django, Ruby on Rails, Node.js, Express.js, Laravel, Spring Boot.
API development: RESTful and GraphQL APIs.
Data structures and algorithms: Efficient data handling and problem-solving.
Version control: Tools like Git for managing code changes.
Cloud platforms: AWS, Azure, or GCP for deploying and managing applications.
development, Java, robust for enterprise-grade applications and financial systems, JavaScript, which is essential for front-end development and web applications, C#, which is used in various fintech applications, especially in the Microsoft ecosystem, and Ruby on Rails, known for rapid development and web applications.
Other technologies might include biometrics for secure authentication (fingerprint, facial recognition), API
Imagine you're at a restaurant. You don't need to know how the kitchen operates or where the food comes from. You simply look at the menu (the API) and order what you want. The waiter (the API) takes your order, communicates it to the kitchen (the system), and brings you the food (the data).
In simpler terms, an API is a set of rules that allows different software programs to talk to each other. It's like a messenger that carries information between two applications. This makes it easier for developers to build new things without having to start from scratch.
For example, a weather app uses an API to get data from a weather service or a social media app uses an API to share content on other platforms. Essentially, APIs allow different software applications to work together seamlessly.
API definition
API (Application Programming Interface) is a set of protocols, routines, and tools for building software applications. It specifies how software components should interact. Essentially, an API acts as an intermediary, allowing different software applications to communicate and share data without requiring knowledge of each other's internal implementation.
How does API work?
An API is a mediator between two software applications, enabling them to communicate and exchange data. This interaction occurs through a request-response cycle.
Request. A client application (like a mobile app or website) sends a request to an API server. The request typically includes specific parameters or data.
Processing. The API server receives the request, processes it based on predefined rules, and accesses the necessary data or performs required actions.
Response. The API server sends a response back to the client, containing the requested data or a status indicating the outcome of the request.
What are the key components of an API?
An API consists of several key components that work together to facilitate communication between software applications. Here are some of them:
Endpoints. These are specific URLs that represent the resources or data accessible through the API. For example, https://api.example.com/users might be an endpoint for retrieving user information.
HTTP methods. These dictate the type of action to be performed on a resource. Common methods include:
GET: Retrieve data
POST: Create new data
PUT: Update existing data
DELETE: Delete existing data
Headers. Additional information sent with the request, such as authentication credentials, content type, and request parameters.
Request body. Data sent to the API server for processing, often in JSON or XML format.
Response. The data returned by the API server, typically in JSON or XML format, along with a status code indicating the success or failure of the request.
Documentation. Detailed information about the API's capabilities, endpoints, parameters, and expected responses.
How do you use API in practice?
Every modern application you use uses APIs. Weather apps use APIs to fetch weather data for different locations. An e-commerce website integrates payment gateways using their APIs to process transactions, and a mapping application incorporates maps and directions using Google Maps API.
Using an API typically involves several steps.
Finding a suitable API. Identify an API that offers the data or functionality you need. Popular platforms like Google, Twitter, and many others provide public APIs.
Understanding the API documentation. Carefully read the API documentation to learn about endpoints, parameters, request formats, and expected responses.
Obtaining necessary credentials. Some APIs require authentication, so you'll need to obtain API keys or tokens.
Making API calls. Use programming languages (like Python, JavaScript, or Java) to construct HTTP requests to the API's endpoints.
Parsing the response. Process the data returned by the API to extract the desired information.
Handling errors. Implement error handling mechanisms to gracefully handle unexpected responses or API failures.
Remember that most APIs have usage limits, so be mindful of your request frequency. Handle sensitive data securely, comply with relevant regulations, and be prepared for API changes and updates.
integration to connect different financial systems and services, and data analytics for extracting insights from financial data. The choice of technologies depends on the specific fintech product or service being developed.
What kind of specialists do you need for a FinTech project?
Building a successful fintech product requires a diverse team of specialists. You will need both technical and business specialists. Among them:
- Software engineers to develop the core functionalities of the fintech application.
- Data scientists to analyze financial data to extract insights and build predictive models.
- Blockchain developers for projects involving cryptocurrencies or distributed ledger technology.
- Security experts to ensure the protection of sensitive financial data.
- UI/UX designers to create user-friendly interfaces.
- Financial analysts to understand financial markets and products.
- Product managers to define product vision and roadmap.
- Compliance officers to ensure adherence to financial regulations.
- Risk managers to assess and mitigate financial risks.
« Back to Glossary Index

